Hi Cristobal,
I believe this is the relevant OneLogin documentation page:
Use the OneLogin SAML Test Connector
You should use this connector option by default, as Laserfiche requires an Service Provider (SP) initiated SAML flow. IDP initiated SAML auth is still supported if you set a Landing Page in LFDS, but SP initiated is required.
SAML Test Connector (SP): This is the basic SP Initiated connector that contains the general URL fields that will be used to pass the connector information between OneLogin and the application in question.
Unless you want OneLogin to encrypt the assertion in the SAML Response in addition to cryptographically signing it (usually overkill as the response is already going over encrypted HTTPS), in which case you should start with this option:
SAML Test Connector (SP) w/Public Cert: Along with all the functionality of the basic SP connector, this version includes an encrypted assertion.
On the Laserfiche Directory Server (LFDS) side, first ensure you have your STS site(s) registered correctly under Settings > STS Sites.
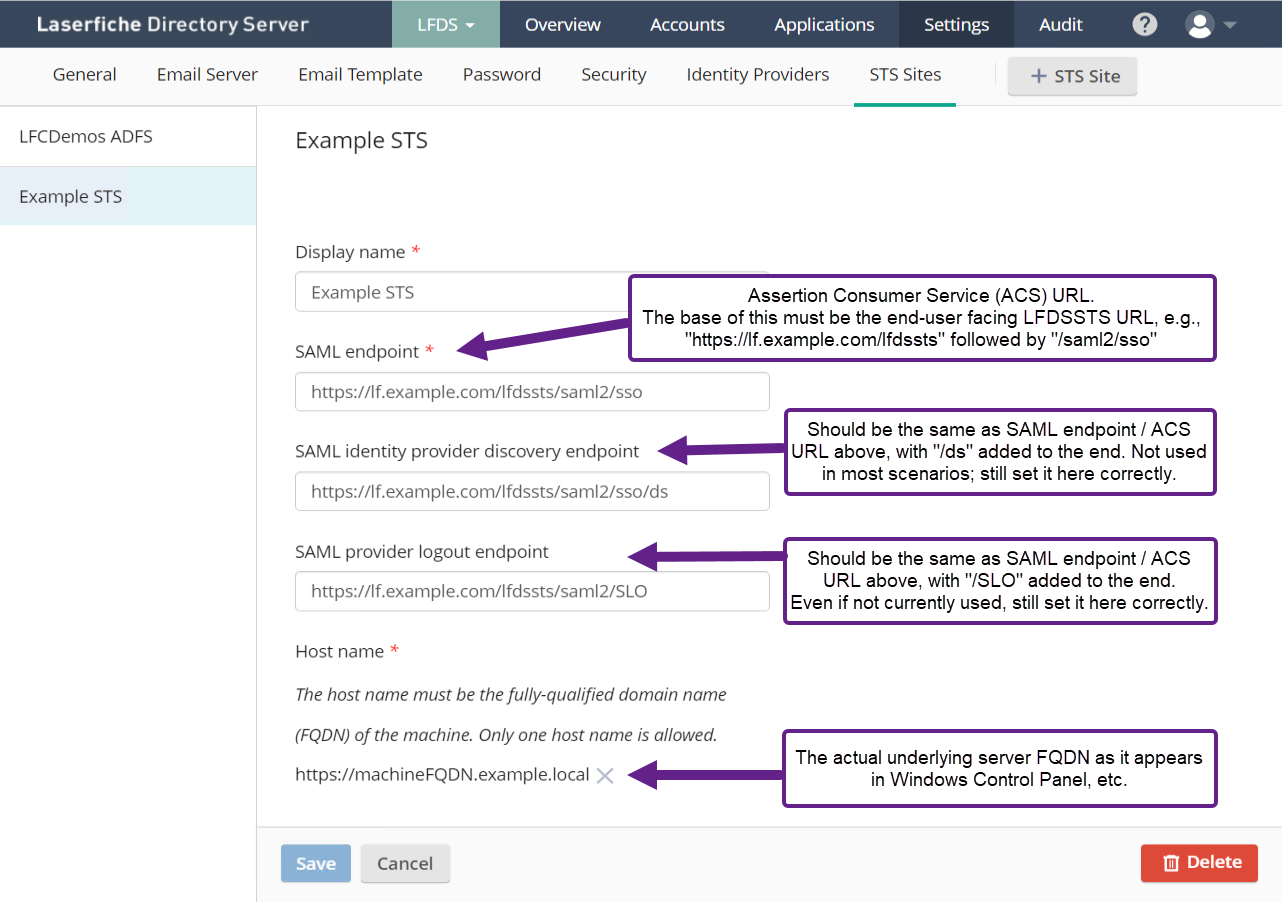
The OneLogin ACS (Consumer) URL field is simply the "SAML endpoint" value from the STS Site configuration in Directory Server. Their description is "This field will contain the address where the SAML response is posted to.", which for Laserfiche is the STS Site SAML endpoint. The ACS URL is a universal field for all SAML configurations because the IDP always needs to know where to send the SAML Response.
The OneLogin ACS (Consumer) URL Validator field says:
This field is used by OneLogin to ensure that we POST the response to the right place. If the response is Service Provider (SP) initiated, they will provide the URL to POST the SAML response to.
Basically, the ACS (Consumer) URL Validator will take the form of the ACS (Consumer) URL, however it will be "escaped out," meaning that all periods and backslashes will have forward slashes immediately preceding them.
Creating a secure ACS (Consumer) URL Validator value is key to the security of the connector. If setup is misconfigured, an attacker could forge Authentication Requests to serviceprovider.com (SP).
For example, consider this ACS (Consumer) URL:
https://serviceprovider.com/saml/consume/
A secure ACS (Consumer) URL Validator regular expression would be:
^https:\/\/serviceprovider\.com\/saml\/consume\/$
Note the essential anchors: ^ and $.
Here is an example of an insecure ACS (Consumer) URL Validator regular expression:
https:\/\/serviceprovider\.com\/saml\/consume\/
This insecure ACS (Consumer) URL Validator could be bypassed with an ACS (Consumer) URL of:
http://www.evil.com/saml/consumer?getparam=https://serviceprovider.com/saml/consume/
So following their example, this ACS URL would have the following OneLogin secure ACS URL Validator (backslashes and periods escaped and with start and end anchors; this is regex) and SLO URL:
For their optional Single Logout (SLO) URL field, you would enter the LFDS STS Site "SAML provider logout endpoint" value, which ends with "/SLO".
Hope that helps!
-Sam