It's really hard to say exactly what's happening because the folder structure can be a factor, and "inherited rights" could be disabled on one or more subfolders, which is part of the reason deny isn't the best way to do this.
The better way to restrict them to a specific folder is to ensure that access to your folders/content is not automatically given to Everyone; ideally, your access rights should always require an explicit Allow.
Basically, you should be telling Laserfiche what users are allowed to see and do in most, if not all, instances rather than telling it what they shouldn't see.
What I always do at a minimum is remove all "Everyone" permissions from the repository or only allow Everyone to see the root with "this entry only" access.
Next, I set up repository groups that manage access to different folders, content, features, etc.; this way I rarely have to go in and set access on entries directly.
Then, I just add users or groups to those repository groups. For example, if we want our help desk people to have read only access to Fiscal folders, I just add the Help Desk LFDS group to the "Fiscal - Read Only" repository group.
As a result, I don't have any LFDS groups, users, etc. configured directly in the access rights; it is all handled by the repository groups. Another benefit of this is that editing access rights on the folders/entries requires updates to the ACL tables and can be slow in larger repositories.
On the other hand, adding/removing users from groups is super fast because it doesn't change the ACL tables it just links the user to the existing permissions.
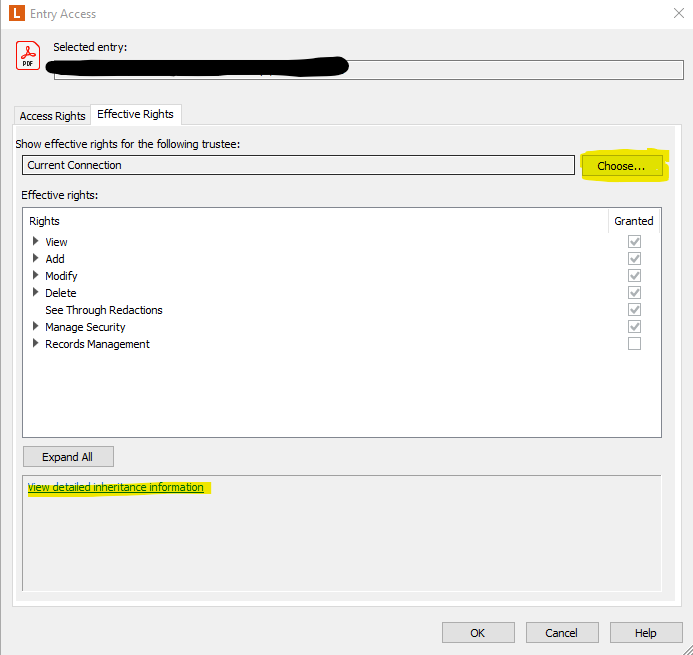
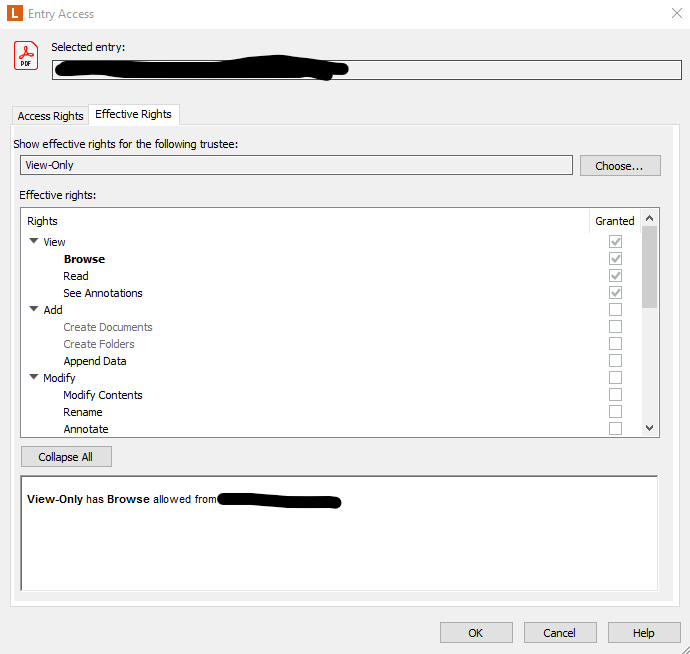
In the mean time, one other thing you could do is find an entry they shouldn't be allowed to find via search yet still are, right-click it and check the access rights, choose the user your are having issues with, then do an effective permissions check, which should show you the inheritance information.