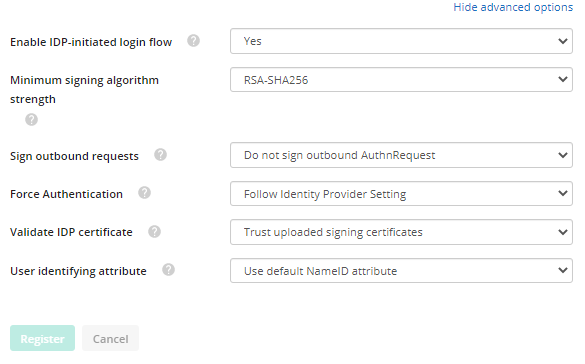
It was brought to my attention that AD FS does not appear to have a Federated ID associated with a user account and I did a quick Google search myself to see if any articles were discussing a federated id in context to AD FS users. It doesn't seem like a thing.
So how would we fill out this box when enabling Single Sign-On for AD FS idenitity providers?