The simplest way to restrict access to the /LFDS web app on a server that is otherwise exposed to the internet is using the IIS IP and Domain Restrictions feature. This approach requires no additional servers, software, or security appliances. Restrict access to the /LFDS web app to at minimum only private network IP address space:
- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
I highly advise doing this for single-server systems that must have other Laserfiche web apps internet accessible. It takes less than five minutes to configure and effectively closes a significant attack surface. Consider doing the same for /FormsConfig, (WebLink) /Designer, and other backend/admin IIS web apps that shouldn't be publicly exposed. Anyone who needs to access these backend/admin web apps can do so through a VPN or other such secure access method to the internal network.
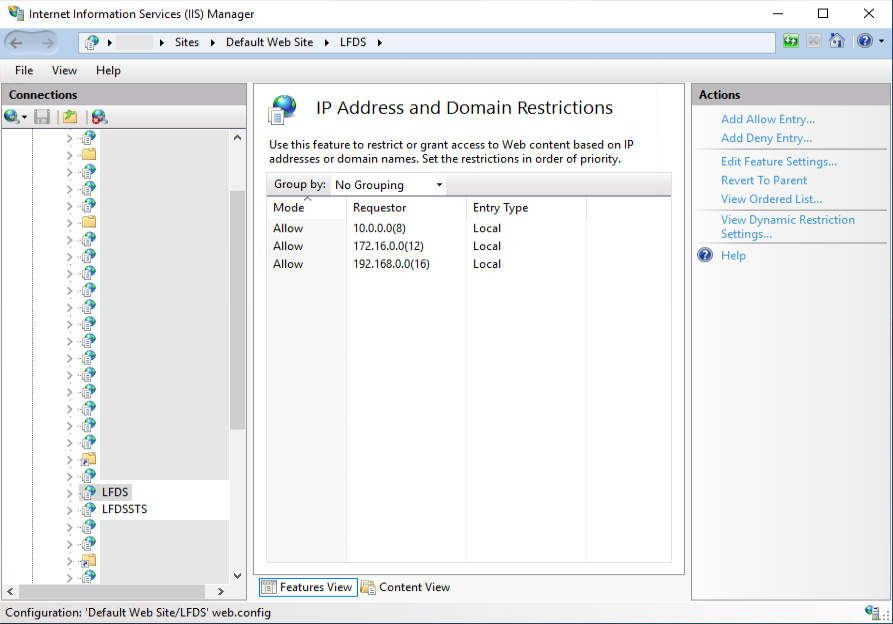
Restricting web app access to internal IP ranges using this feature doesn't make it impossible for an outside attacker to reach, though it does make it significantly harder because they have to pull off a TCP IP spoofing attack before reaching the authentication step.
In any event, it technically possible to remotely authenticate to LFDS over the internet from a workstation on an untrusted domain by entering AD credentials in UPN format for a user with LFDS web admin access rights into the 401 auth challenge prompt. Just did so with one of my test servers. The credentials were sent in plaintext using NTLM because Kerberos doesn't work over the internet.
The customer may have global AD WinAuth security controls that block authentication from outside networks (a very rational thing to implement), the LFDS IIS web app may be configured in a way (custom app pool identities, etc.) that's breaking WinAuth, or something else.