It looks like this is the documentation page you're referencing: https://doc.laserfiche.com/laserfiche.documentation/11/administration/en-us/Default.htm#../Subsystems/LFAdmin/Content/SSL_TLS_Client.htm
The following is a detailed explanation if you're interested and aren't very familiar with how certificates work (most people aren't). If you simply want the short answer, it's "the public Forms server must have a web server TLS certificate from a publicly trusted Certificate Authority bound to port 443 for HTTPS".
Clients validate TLS certificates by checking what's known as a "chain of trust", which starts with your certificate, has some number of "Intermediate Certificates" in the middle, and ends with a "Root Certificate Authority".
By way of analogy: Your drivers license/ID (certificate) is issued by the state DMV (intermediate cert) which is given its authority by the State Govt. (root cert authority). In order for other people to trust the validity of your ID, they need to (a) see that it was issued by the DMV/state, and (b) trust the DMV/state (intermediate and root certs). The first attribute is what makes your govt-issued ID different from a fake ID. When someone checks your ID, they accept it because they acknowledge the legitimacy of the parties who issued it, not because they have a list of every valid ID.
So how does this relate to TLS/HTTPS with websites, like your public Forms instance? It means that you need to ensure your public-facing website has a certificate issued by a publicly-trusted Certificate Authority (CA). Publicly-trusted CAs are those that most operating systems and browsers trust by default, like Digicert, Sectigo, Let's Encrypt, etc. When you visit google.com, amazon.com, or any other public website over HTTPS and don't receive a TLS certificate warning, that's because those websites are using certs issued by publicly-trusted CAs.
By way of example, here's a certificate issued by the public CA DigiCert showing the issuing chain:
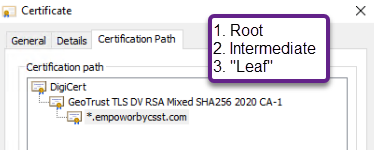
Because nearly every computer in the world trusts that DigiCert root certificate by default, all you need for secure HTTPS communication to your public Forms instance is a similar certificate bound to port 443 in IIS on your Forms server.