Changelog:
Update May 15, 2025: Added variant of modified checkAutoLogin() function that (a) allows sending users to a specific URL after signing out, and (b) automatically selects the first available federated IDP without having to specify it by name.
Update Feb 7, 2024: Laserfiche Directory Server 11 Update 5 (released 19 Oct 2023) introduced native support for SAML SLO. Documentation: Configuring Single Logout (SLO) with SAML Authentication
Update July 7, 2021: Instructions on implementing Single Log Out (SLO) with AD FS
_____________________________
Hi Bert,
There are three parts to accomplishing what you're asking about.
Automatically selecting the Federated (AD FS) option on the STS login page:
Note that this works for any federated IdP (SAML) in addition to AD FS.
- On the server where STS is installed, open file Explorer and navigate to ".\Program Files\Laserfiche\Directory Server\Web\WebSTS\Views\Home"
- Make a backup copy of the "Login.cshtml" file and name it "Login-Original.cshtml" or similar
- Open "Login.cshtml" in a text editor of your choice
- Find the function called: "function checkAutoLogin()"
- Replace it with one of these modified versions.
Version 1: Explicitly set federated IDP, no logout redirect (goes back to STS login page). "IdPNameExactlyAsItAppearsInLFDS" (in LFDS web admin -> Identity Providers) is hopefully self-explanatory. For AD FS, it is the associated AD IdP name you have AD FS enabled for.
function checkAutoLogin()
{
{
var logoutMarkup = getCookie("lfdsstsLogoutMarkup");
if (!logoutMarkup)
{
login(AuthType.Federation, "IdPNameExactlyAsItAppearsInLFDS")
}
}
};
Version 2: Dynamically selected federated IDP (picks "first in the list"), redirects to the specified LogoutRedirectURL on logout. Update "https://example.com" with your own URL.
function checkAutoLogin()
{
{
var logoutMarkup = getCookie("lfdsstsLogoutMarkup");
var LogoutRedirectURL = "https://example.com/";
if (!logoutMarkup)
{
login(AuthType.Federation, "@Model.FederationLoginOptions[0].ProviderName");
}
else
{
window.open(LogoutRedirectURL,"_self")
}
}
};
You can of course swap in the explicit federated IDP version of the login() function parameter if desired. The
- Open the "Embedded.cshtml" file in the same directory and replace the autoLoginFunction there as well.
- Recycle the LicenseManagerSTS IIS Application Pool for the change to take effect.
[Optional but recommended]
Configure AD FS Single Log Out (SLO)
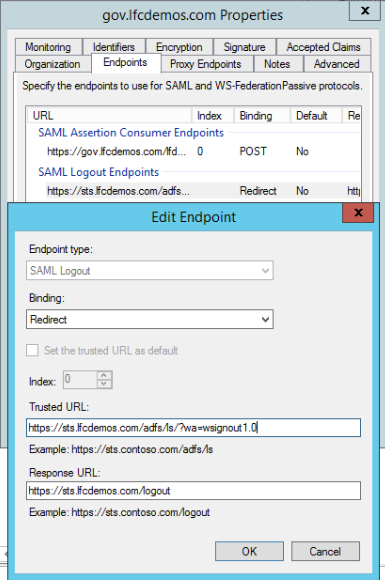
- In AD FS, open the Relying Party Trust for Laserfiche and go to the "Endpoints" tab
- Add a new SAML endpoint, with the following properties:
- Endpoint type: SAML
- Binding: Redirect
- Trusted URL: https://your-adfs-endpoint.example.com/adfs/ls/?wa=wsignout1.0
- Response URL: https://your-adfs-endpoint.example.com/logout
- Example screenshot:
- Updated post 7 Feb 2024 noting Laserfiche has native SAML SLO support as of LFDS 11 Update 5. Use that instead of this workaround.
In the WebSTS Login.cshtml and Embedded.cshtml files described in the section above, replace the checkAutoLogin function with this version that includes both automatic IdP selection and the SLO redirect call. Make sure to update both the IdP name and samlLogoutURL (the "Trusted URL" from the previous step) placeholder values.
function checkAutoLogin()
{
{
var logoutMarkup = getCookie("lfdsstsLogoutMarkup");
if (!logoutMarkup)
{
login(AuthType.Federation, "IdPNameExactlyAsItAppearsInLFDS")
}
else
{
var samlLogoutUrl = "https://your-adfs-endpoint.example.com/adfs/ls/?wa=wsignout1.0";
window.location = samlLogoutUrl;
}
}
};
- Open the "SignOut.cshtml" in the same directory and find the "setLogoutMarkup" function. This sets the "lfdsstsLogoutMarkup" cookie we use to detect logout vs login. Within it there is a line reading:
" var lifeTime = 1;"
Update its value from "1" to "0.2" to change its lifespan from one minute to twelve seconds (0.2 min). With the auto-login plus SLO version of the code, you cannot attempt to log back in until this cookie expires. Twelve seconds should be long enough for even slow browsers/connections.
Configure AD FS to Always Require Authentication
Note: Implementing SLO as described above is at some level a client-side method of achieving a similar security goal. A dedicated attacker can trivially circumvent client-side SLO by blocking the redirect to the SLO endpoint in their browser. The method described below is enforced server-side and should be considered a required complimentary security measure for publicly-accessible sites, and an optional one for intranet-only sites.
Because logging out of LFDS only invalidates the Laserfiche STS token and not the AD FS token, it is important to configure the AD FS Relying Party Trust for Laserfiche to Always Require Authentication. This prevents someone using the same AD FS token to log back into Laserfiche without having to re-authenticate.
For step-by-step instructions, please see my post here:
Laserfiche Answers: Force Reauthentication with AD FS
Set the LFDS STS token duration
- On the server where STS is installed, open a supported browser and go to https://localhost/LFDSSTS/configuration
- Set the "Default session timeout (minutes):" field to the desired duration. The default is 1440 minutes (24 hours)
- Click "Update" to save any changes
Other relevant settings
- Repository: Idle Disconnect (timeout) settings (affects all clients)
- Forms: Session idle timeouts (important note: Forms session timeouts trigger logout of all Laserfiche web applications and invalidate a user's current STS token)
I'm working on a way to have logging out in Laserfiche also kill the AD FS token (which is a bit more elegant than enabling Always Require Authentication in AD FS) and will update this post if and when I sort that out. Note: Updated post 7 July 2021 with this solution (SLO).
Let me know if that helps and please mark this as the Answer if it addresses your question.
Cheers,
Sam